Digital transformation represents a significant shift in the way an IT company operates, affecting everything from operations to customer engagement. As organizations increasingly rely on digital technologies, the risk of cyber threats and data breaches grows.
That’s why ensuring the protection of digital assets and maintaining data integrity is critical to the success of any digital transformation initiative.
Let’s talk about nine essential measures that you can implement to enhance your company’s cybersecurity posture, mitigate risks, and secure valuable information against potential threats.
1. Robust cybersecurity framework
A comprehensive cybersecurity framework is essential for protecting digital assets. This involves:
- Risk assessment:Conduct regular risk assessments to identify vulnerabilities and potential threats.
- Security policies:Develop and enforce security policies that outline acceptable use, data protection, and incident response procedures.
- Compliance:Ensure adherence to industry standards and regulations such as HIPAA, GDPR, NIST and ISO/IEC 27001.
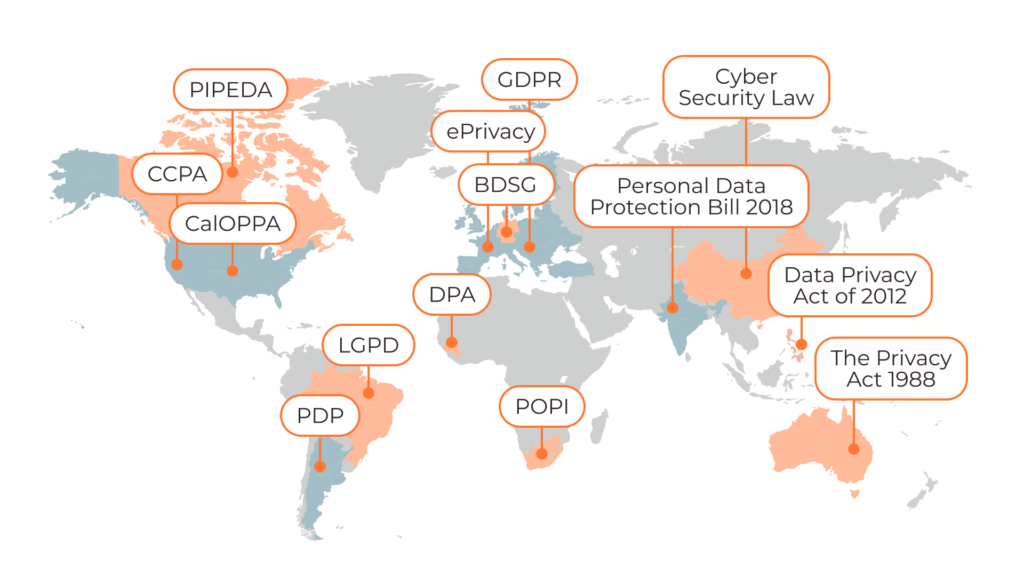
HIPAA (Health Insurance Portability and Accountability Act)
For the organizations operating within the healthcare industry in the United States, compliance with HIPAA is essential. HIPAA focuses on the protection and confidential handling of protected health information (PHI). It establishes national standards to ensure that individuals’ medical records and other personal health information are properly protected while allowing the flow of health information needed to provide high-quality health care. HIPAA mandates several key practices to safeguard data integrity and privacy.
GDPR (General Data Protection Regulation)
GDPR is a regulation in EU law on data protection and privacy for all individuals within the European Union and the European Economic Area. It also addresses the transfer of personal data outside the EU and EEA areas. GDPR aims to give control to individuals over their personal data and to simplify the regulatory environment for international business by unifying the regulation within the EU.
ISO/IEC 27001
ISO/IEC 27001 is an international standard for managing information security. It provides a framework for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). This standard is essential for any organization that wants to systematically manage sensitive company information to remain secure. The standard includes requirements for the assessment and treatment of information security risks tailored to the needs of the organization.
NIST Cybersecurity Framework (CSF)
The National Institute of Standards and Technology (NIST) Cybersecurity Framework provides a comprehensive policy framework for managing cybersecurity risks. It is organized into five key functions: Identify, Protect, Detect, Respond, and Recover. This framework helps organizations understand and improve their management of cybersecurity risk.
2. Secure cloud solutions
As organizations migrate to the cloud, securing cloud environments is critical:
- Cloud security posture management (CSPM):Use CSPM tools to ensure cloud configurations comply with security policies. Datadog for example runs continuous configuration checks across your cloud accounts, hosts, and containers. Receive frequent report summaries of your conformance to industry benchmarking rules, including CIS, PCI, SOC 2, HIPAA, and GDPR.
- Identity and access management (IAM):Implement IAM solutions to control access to cloud resources. Every cloud vendor, whether AWS, Azure, or GCP, has an identity & access management (IAM) service that controls cloud authentication and authorization for all other cloud services across the platform.
3. VPN software
VPNs (Virtual Private Networks) are essential for securing remote connections:
- Encrypted connections:VPNs encrypt internet traffic, protecting data from interception and ensuring secure communications.
- Remote access:VPNs allow employees to securely access company resources from remote locations, essential for a distributed workforce.
- Privacy protection:VPNs hide IP addresses, enhancing privacy and preventing unauthorized tracking of online activities.
VPNs encrypt data transmissions between remote locations and the central servers, protecting against unauthorized access and ensuring that sensitive health information remains confidential. This is particularly important for healthcare providers offering telehealth services or accessing patient records from remote locations.
Virtual Private Network (VPN) software plays a critical role in maintaining GDPR compliance by encrypting data transmissions and securing remote access to personal data in the EU. This helps prevent unauthorized access and data breaches, ensuring that personal data remains confidential and protected, especially when accessing data from remote locations. As we can notice, VPN software is quite usable in building a more robust cybersecurity system.
4. Data encryption
Encryption ensures that even if data is intercepted, it remains unreadable without the appropriate decryption key. Encryption is a fundamental security measure to protect sensitive data:
- Encryption at rest and in transit:Encrypt data both at rest (stored data) and in transit (data being transferred) to prevent unauthorized access.
- Advanced encryption standards (AES):Utilize strong encryption algorithms like AES to ensure data security.
5. Multi-factor authentication (MFA)
Implement MFA to add an extra layer of security beyond just passwords. MFA requires users to provide multiple forms of verification to gain access to systems, reducing the risk of unauthorized access.
- Two-factor authentication (2FA):Require users to provide two forms of identification before accessing sensitive systems.
- Biometric authentication:Incorporate biometric authentication methods such as fingerprint or facial recognition for enhanced security.
6. Regular software updates, audits and patch management
Conduct regular security audits to identify and address vulnerabilities. Audits help ensure that security measures are up-to-date and effective against evolving threats. Maybe using Setronica external code review can come handy in checking the quality of your software solution. Keeping software up to date is crucial to prevent cyberattacks:
- Patch management:Regularly update and patch software to fix vulnerabilities.
- Automated updates:Use automated update systems to ensure timely application of patches.
7. Employee training and awareness
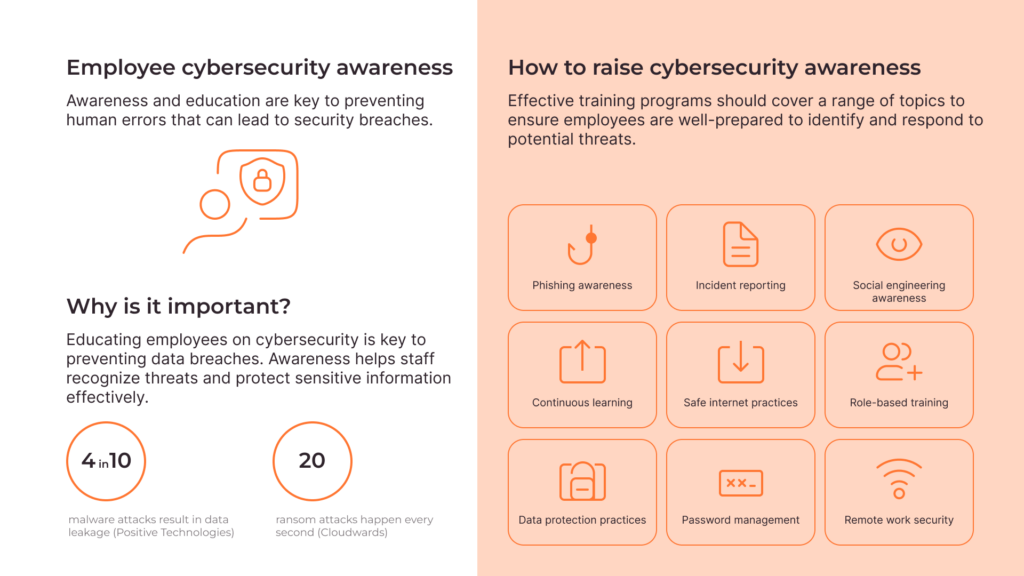
Train employees on cybersecurity best practices, such as recognizing phishing attempts, using strong passwords, and securely handling sensitive data. Awareness and education are key to preventing human errors that can lead to security breaches. Human error is a significant factor in security breaches. Training employees can mitigate these risks:
- Security awareness programs:Conduct regular training sessions on cybersecurity best practices.
- Phishing simulations:Run simulated phishing attacks to educate employees on recognizing and responding to phishing attempts.
8. Advanced threat detection and response
Use advanced tools and technologies to detect and respond to threats:
- Intrusion Detection Systems (IDS):Implement IDS to monitor network traffic for suspicious activity. IDS and SIEM in on-premise environments are deployed behind a firewall but out of the direct flow of traffic. These systems are designed to passively process copies of data so that they do not affect network performance.
- Security Information and Event Management (SIEM):Use SIEM solutions to collect and analyze security data in real time, enabling rapid response to incidents. Datadog Cloud SIEM takes this visibility a step further by aggregating and analyzing all related log data in order to confirm the source of this activity. For example, Cloud SIEM can help organizations determine if the account initiating these requests is compromised, which would require immediate intervention before an attacker gains access to other resources.
9. Incident response plan
Having a well-defined incident response plan is essential for mitigating the impact of security breaches:
- Incident response team:Establish a dedicated team responsible for handling security incidents.
- Regular drills:Conduct regular drills to ensure the incident response team is prepared to act swiftly and effectively.
Cybersecurity is a cornerstone of any successful digital transformation. By implementing these nine key measures, organizations can protect their digital assets, ensure data integrity, and build a secure foundation for digital growth. Setronica has over 25 years of experience of running business both in the USA and EU. Working under certain regulations and under different law systems, always call for help from legal advisors. Having a lawyer is a must-have in situations where you run a business across different, other than your, countries.
Embracing cybersecurity enhances trust and confidence among participants, and it drives the success of any digital transformation. Cybersecurity hides a lot of its complexity, I hope I revealed some of them. Please, feel free to contact me if you have any further questions via the form below.
FAQ
What role does encryption play in protecting digital assets?
Encryption is critical for securing sensitive data both at rest and in transit. It prevents unauthorized access by converting data into a coded format that can only be deciphered with the correct encryption key, ensuring that even if data is intercepted, it remains unreadable.
Why is employee training important in cybersecurity?
Employee training is essential because human error is a common cause of security breaches. Regular training programs educate employees about the latest cybersecurity threats and best practices, enabling them to recognize and respond to potential security incidents, such as phishing attacks, more effectively.
How does multifactor authentication enhance security?
Chapters
- 1. Robust cybersecurity framework
- 2. Secure cloud solutions
- 3. VPN software
- 4. Data encryption
- 5. Multi-factor authentication (MFA)
- 6. Regular software updates, audits and patch management
- 7. Employee training and awareness
- 8. Advanced threat detection and response
- 9. Incident response plan
- FAQ



